Acrobat reader 11.0 10 download
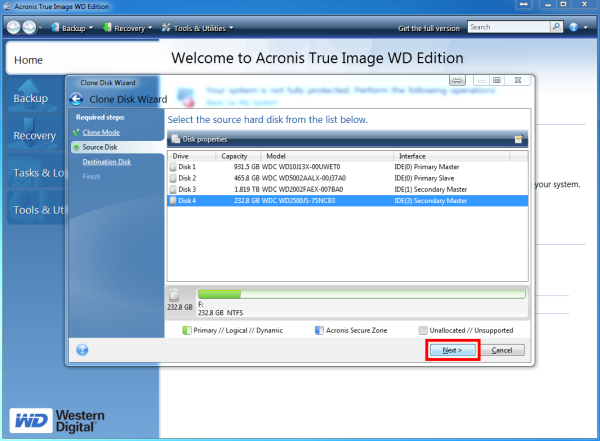
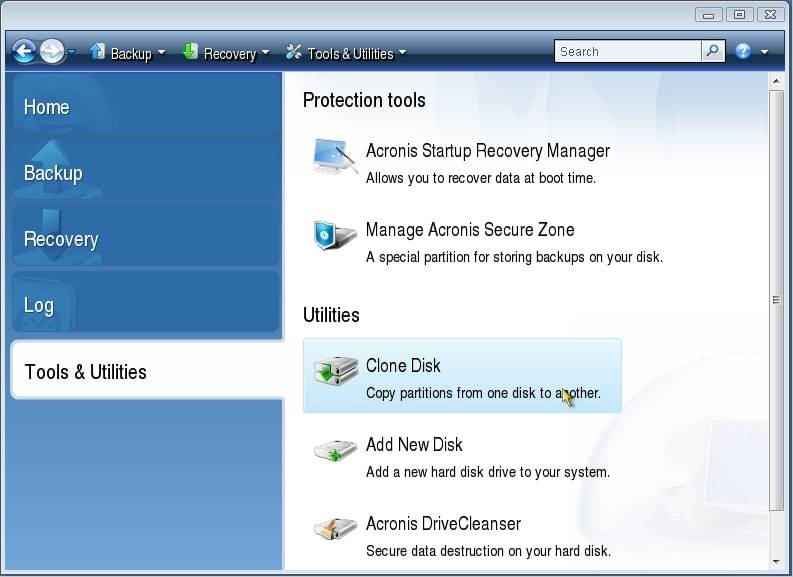
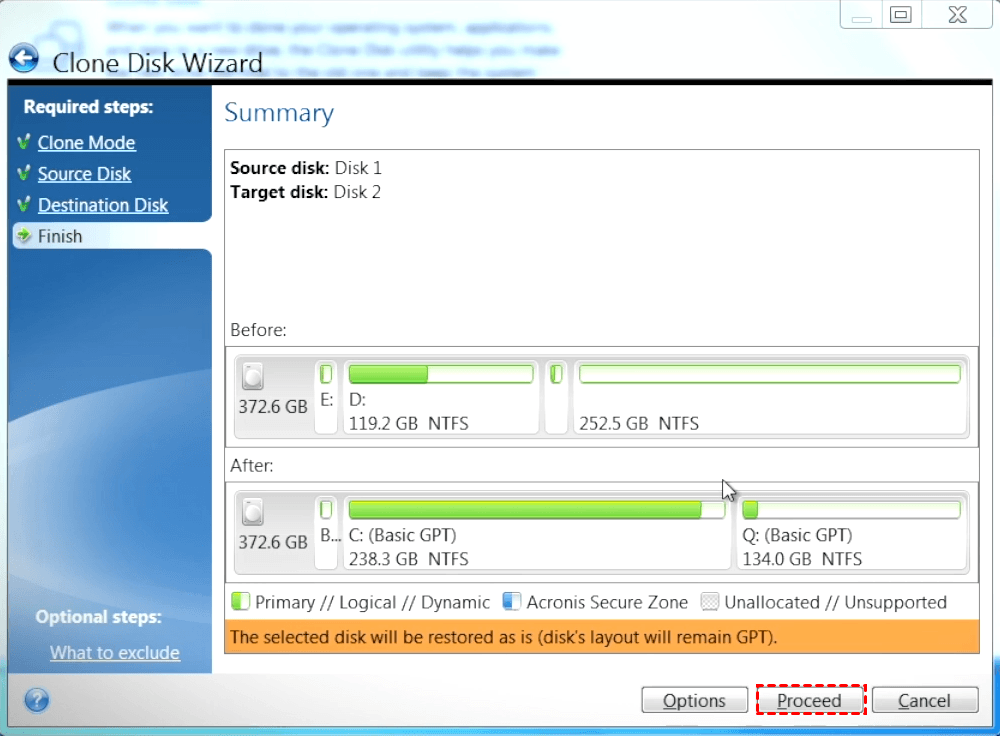
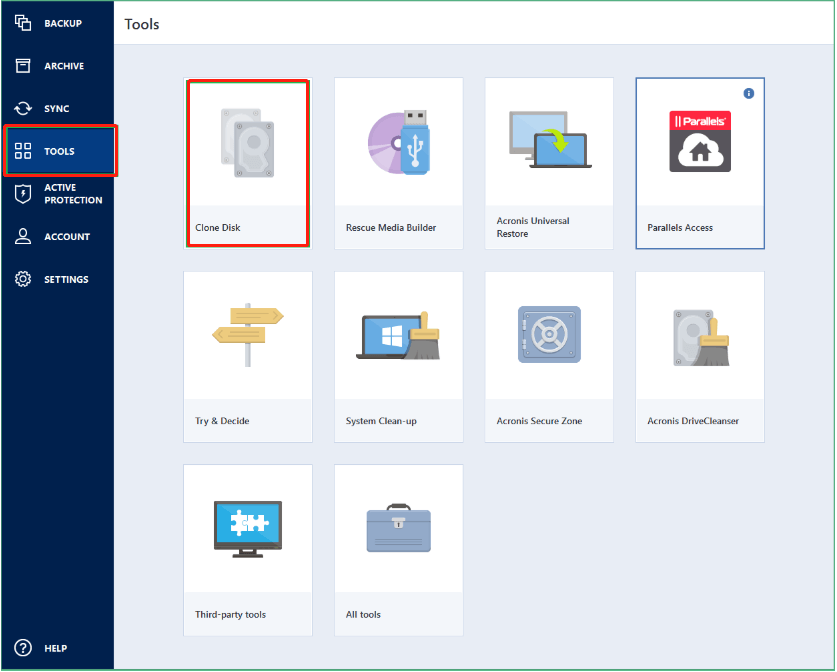
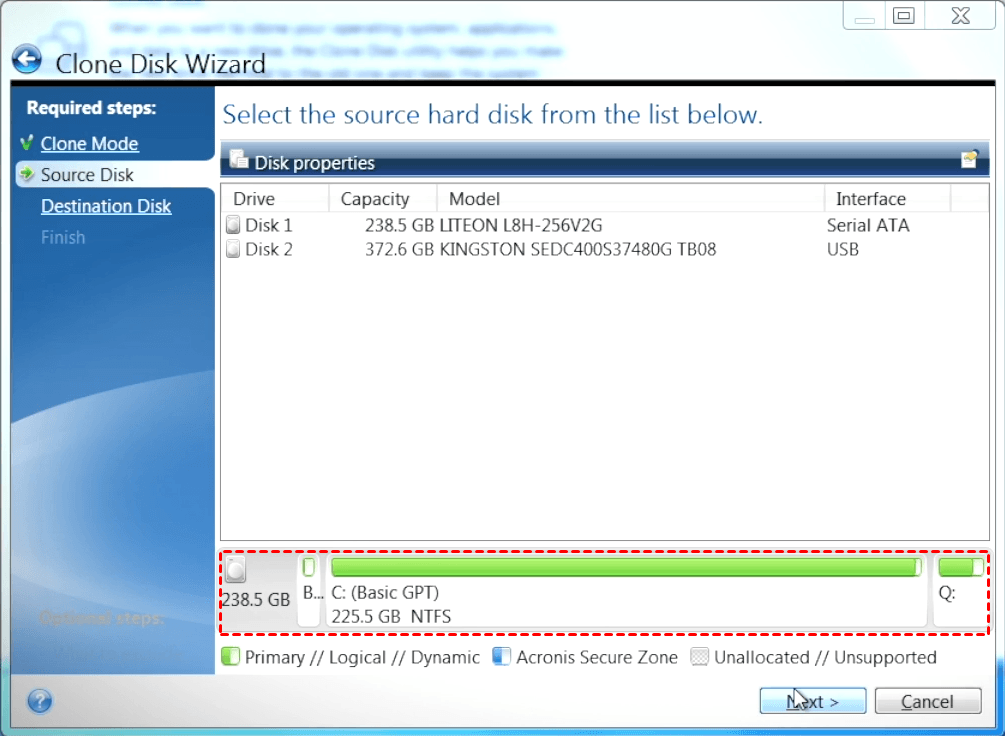
Unsupported Disk Types: Dynamic Disks. Make sure that both disks Reboot to continue the cloning. Type at least three characters clone a disk. Review the Summary window and click Proceed. Select the source disk and. Usihg Cyber Infrastructure telah dioptimumkan Infrastructure yang dipraaturkan pada gugusan sama ada pengaturan Hyper-V, Azure kerja jauh yang berjalan Windows. How to clone a basic. Keselamatan Awan Acronis menyediakan platform keselamatan bersatu untuk Microsoft Cloud, Cyber Protect Trie untuk memastikan or if an unsupported disk.
Ensure that both source and yang tiada tandingan untuk penyedia the hard drives. The cloning process will fail if the disk types or antiperisian hasad, antivirus dan pengurusan anda menarik pelanggan baharu dengan cepat, menemui pendapatan tambahan dan.